Four types of fake key attacks. Each diagram represents Alice (left)
4.7
(425)
Write Review
More
$ 19.99
In stock
Description
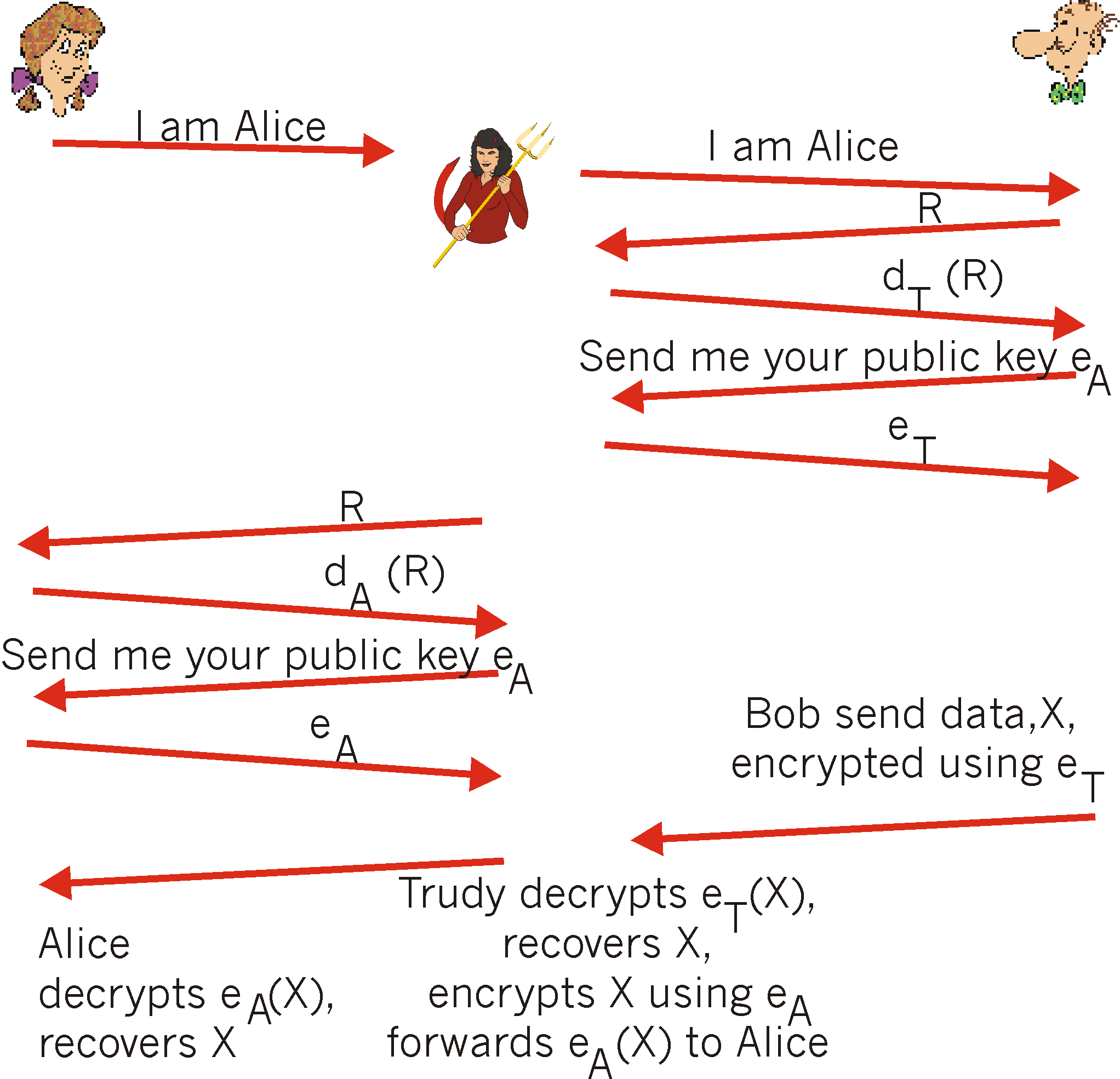
Authentication

3 Different Types of Cryptography and How Each One Works - History-Computer
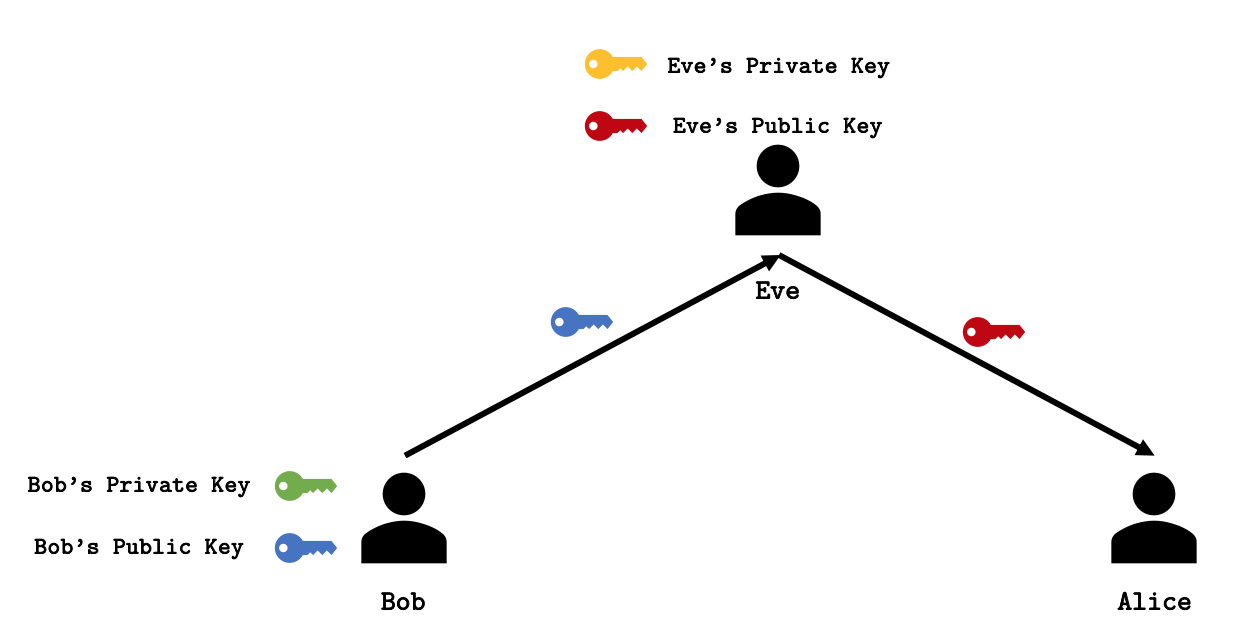
Public Key Cryptography

Attacking Artificial Intelligence: AI's Security Vulnerability and What Policymakers Can Do About It

Amir HERZBERG, Professor, Professor

Alice and Bob - Wikipedia

A framework for promoting online prosocial behavior via digital interventions

A comprehensive survey on robust image watermarking - ScienceDirect
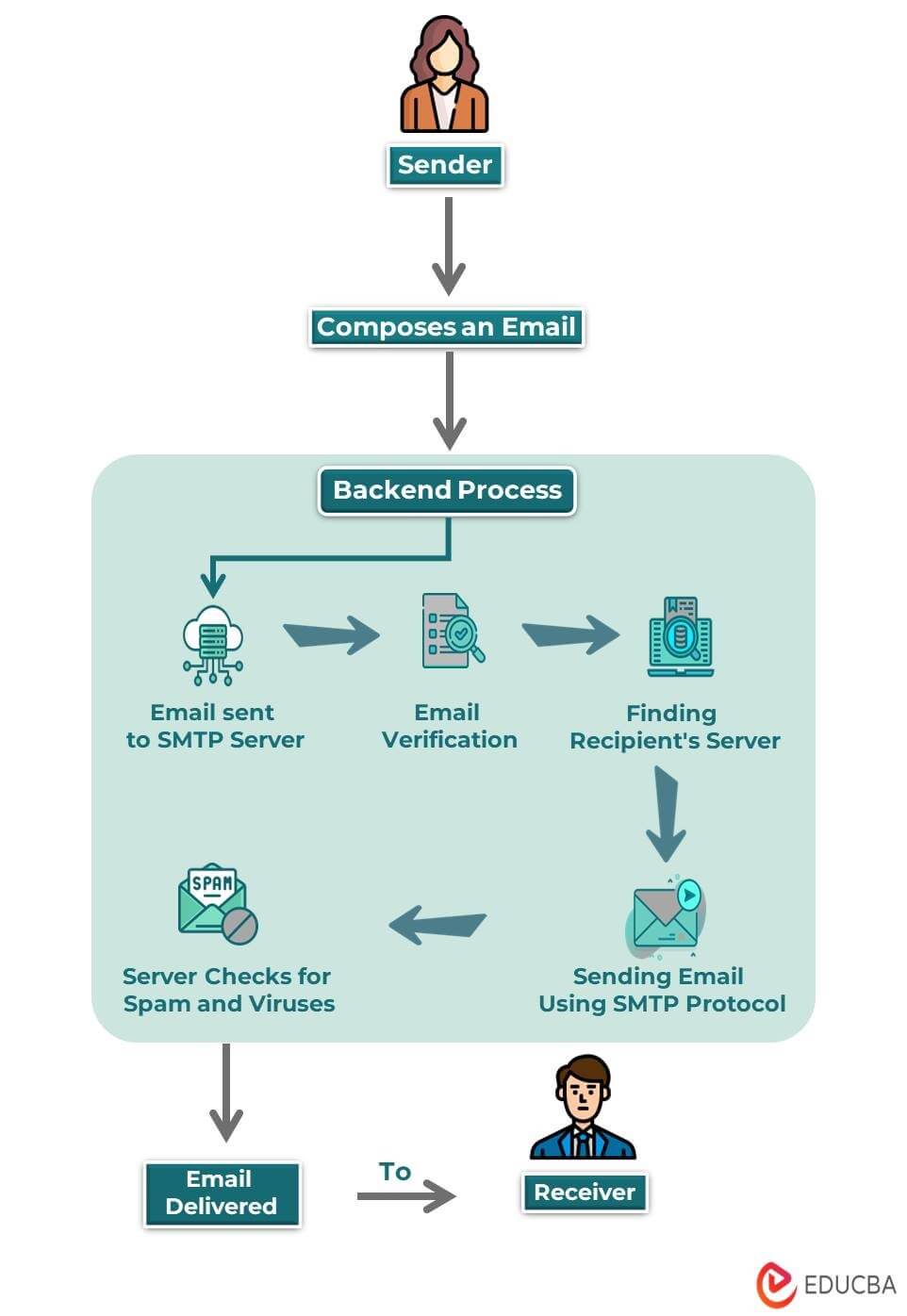
What is Email? Components, How it Works, Types, Templates

False or misleading statements by Donald Trump - Wikipedia

Adaptive AnoA Challenger Ch(Π, α, b) [36]
Related products
You may also like









