Token tactics: How to prevent, detect, and respond to cloud token

What is Token-Based Authentication? Types, Pros and Cons

André Keartland على LinkedIn: Multi-Cloud: Protecting GCP and AWS Applications with Azure WAF

Jeffrey Appel on LinkedIn: Configure Attack Surface reduction and additional protection in Defender

Token theft News and Insights

Token tactics: How to prevent, detect, and respond to cloud token

Microsoft DART (@MicrosoftDART) / X
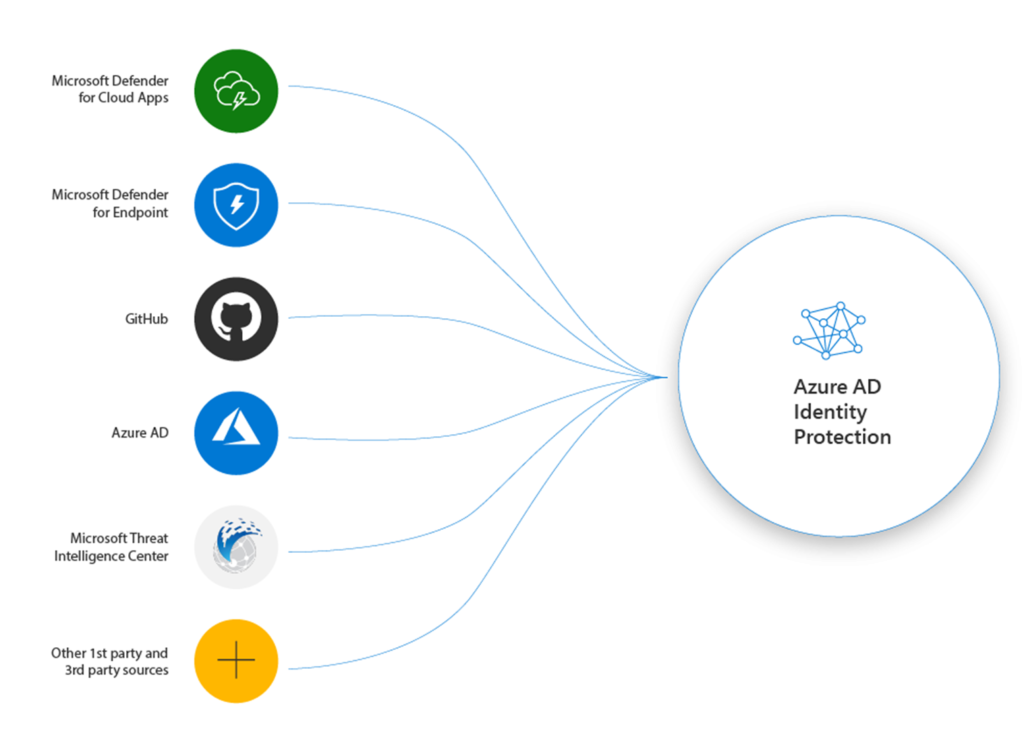
Tips for preventing against new modern identity attacks (AiTM, MFA

Azure AD Conditional Access Token protection (CATP) First
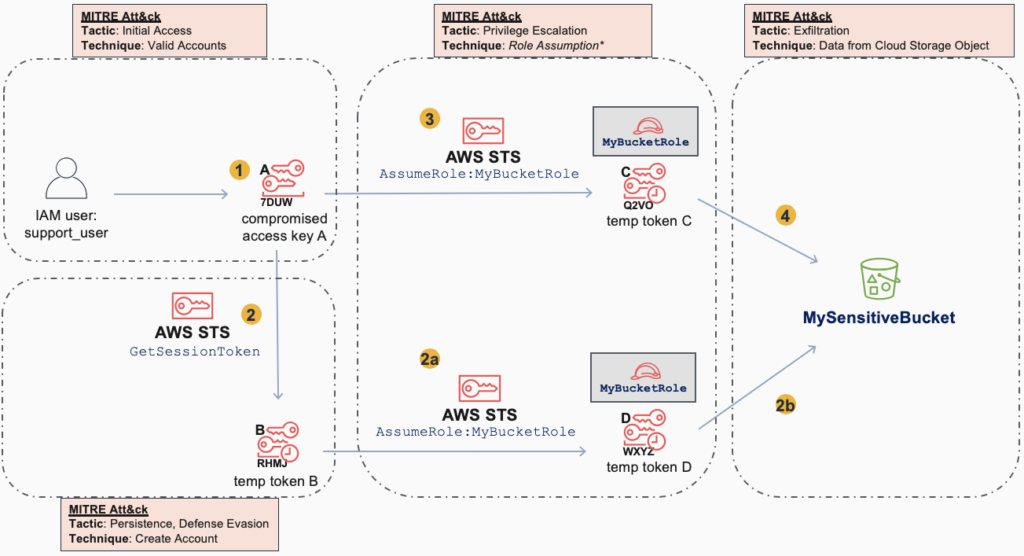
MITRE Att&ck View: Securing AWS Temporary Tokens - Netskope

Matthew Zorich sur LinkedIn : If you are interested in forensics and incident response in the Microsoft…
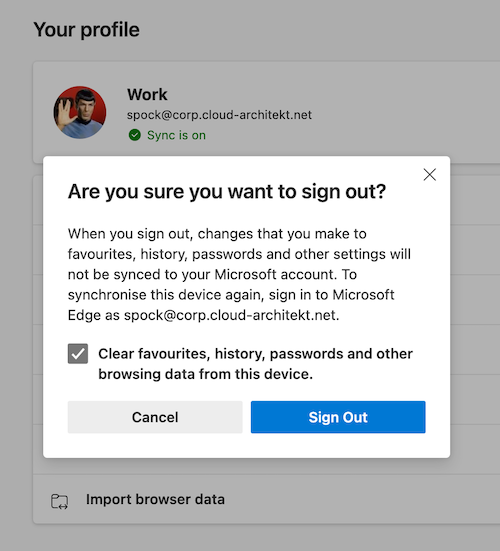
Abuse and replay of Azure AD refresh token from Microsoft Edge in
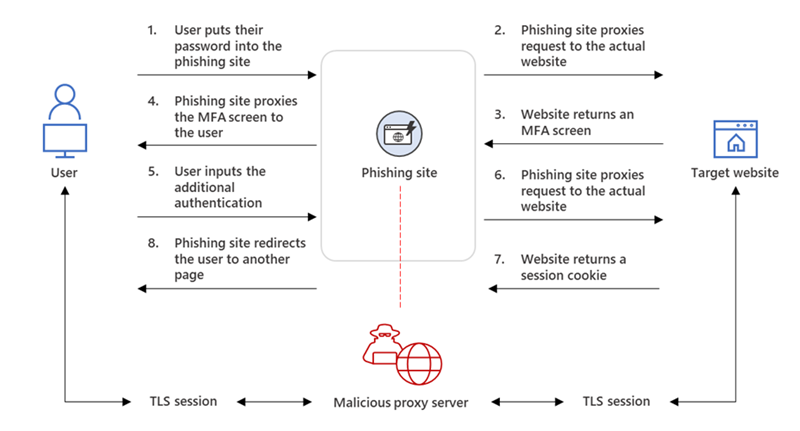
Tips for preventing against new modern identity attacks (AiTM, MFA Fatigue, PRT, OAuth)

QakNote Infections: A Network-Based Exploration of Varied Attack