Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
4.9
(317)
Write Review
More
$ 23.99
In stock
Description

Threat Hunting Beacon Analysis

Threat Hunting DLL-injected C2 Beacons using Memory Forensics

Threat Simulator - Active Countermeasures

About Us - Active Countermeasures
Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
Threat Simulator - Active Countermeasures

Security Considerations of zk-SNARK Parameter Multi-Party Computation, NCC Group Research Blog

Threat Simulator - Active Countermeasures

Sensors, Free Full-Text

Hunt Training - Active Countermeasures
Even More on Threat Hunting
Simulating a Beacon - Active Countermeasures
What Is Threat Hunting and Why Does It Matter?
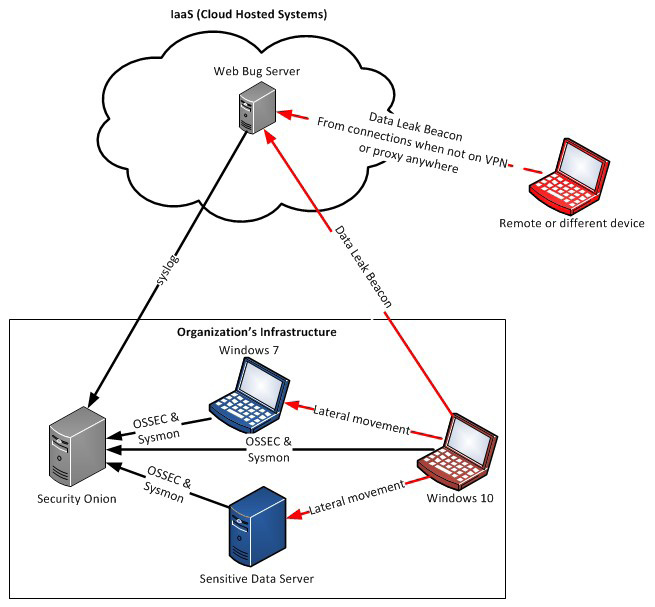
Offensive Intrusion Analysis: Uncovering Insiders with Threat Hunting and Active Defense – CSIAC
You may also like





