
Defending Against Token-Based Threats
4.5
(467)
Write Review
More
$ 24.00
In stock
Description
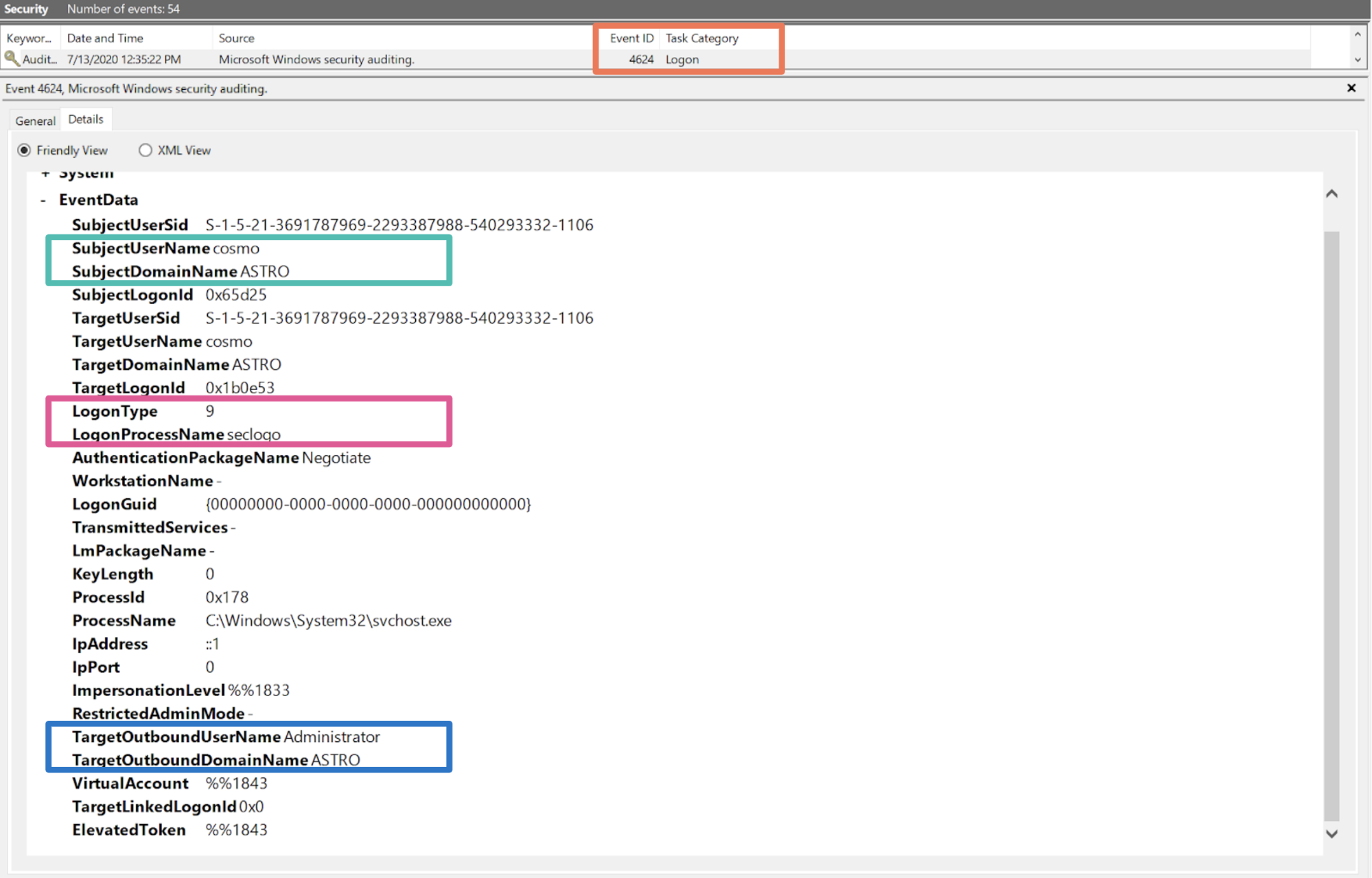
How attackers abuse Access Token Manipulation (ATT&CK T1134
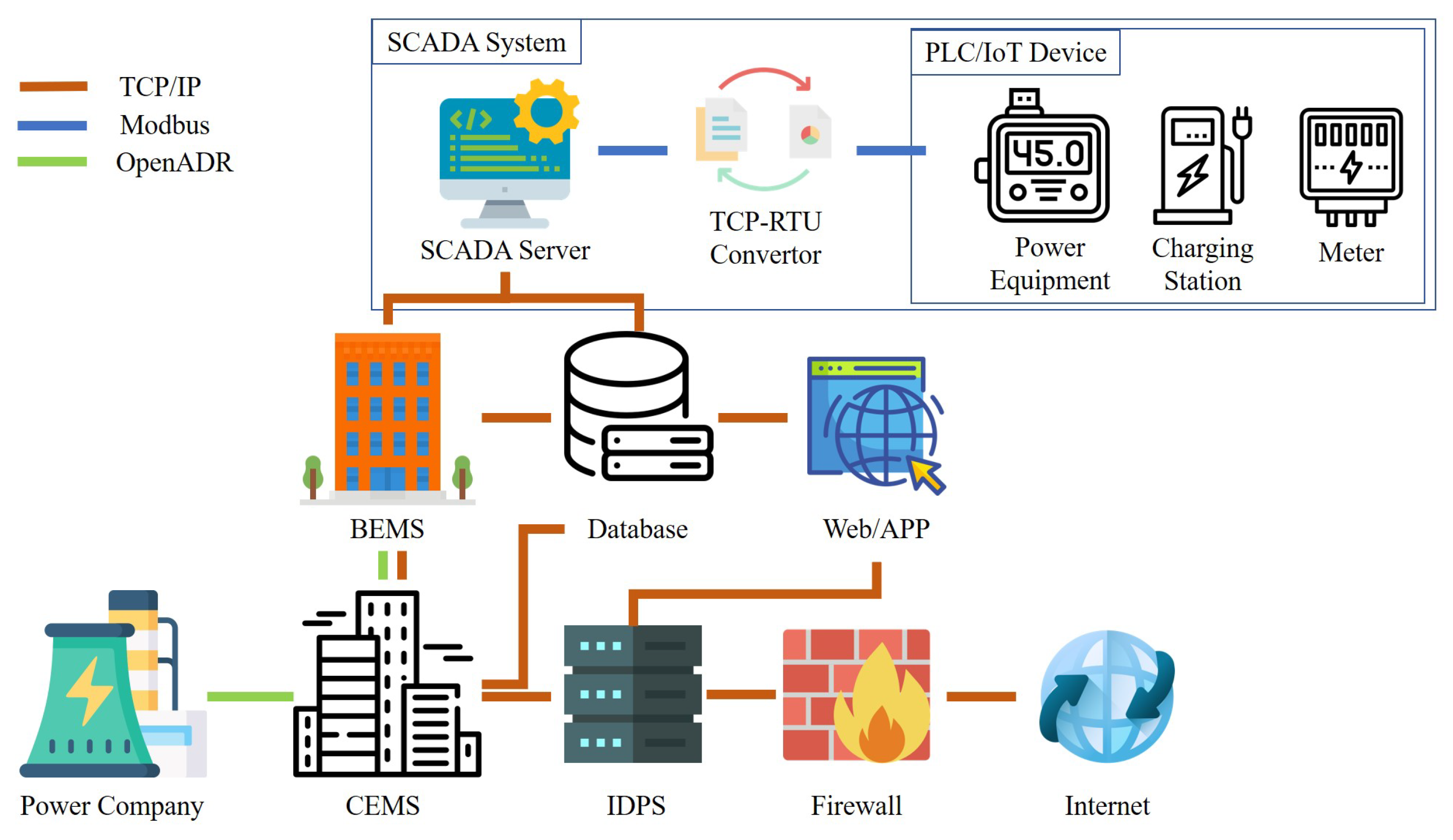
Applied Sciences, Free Full-Text

What is a CSRF Token and How Does It Work?
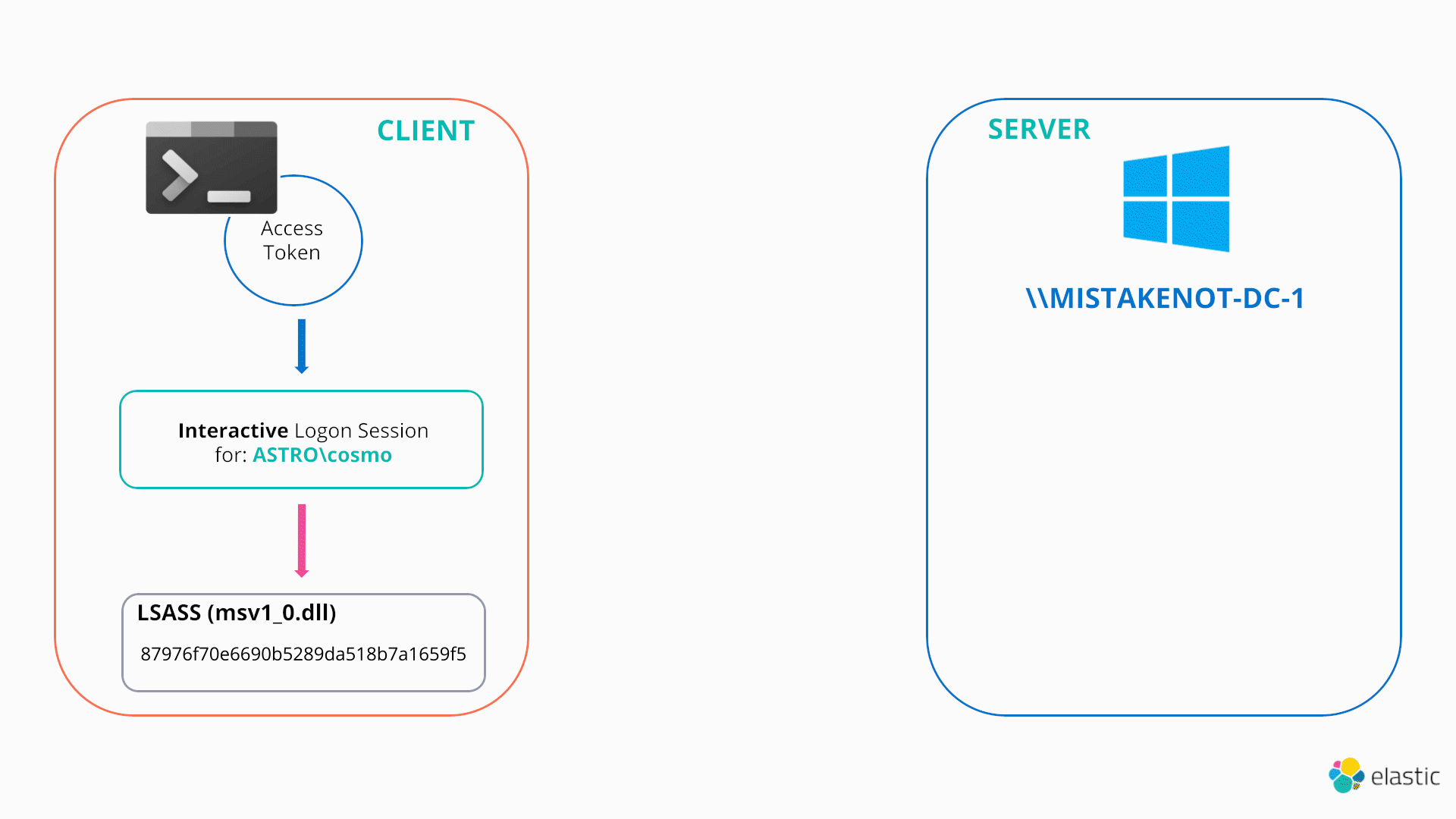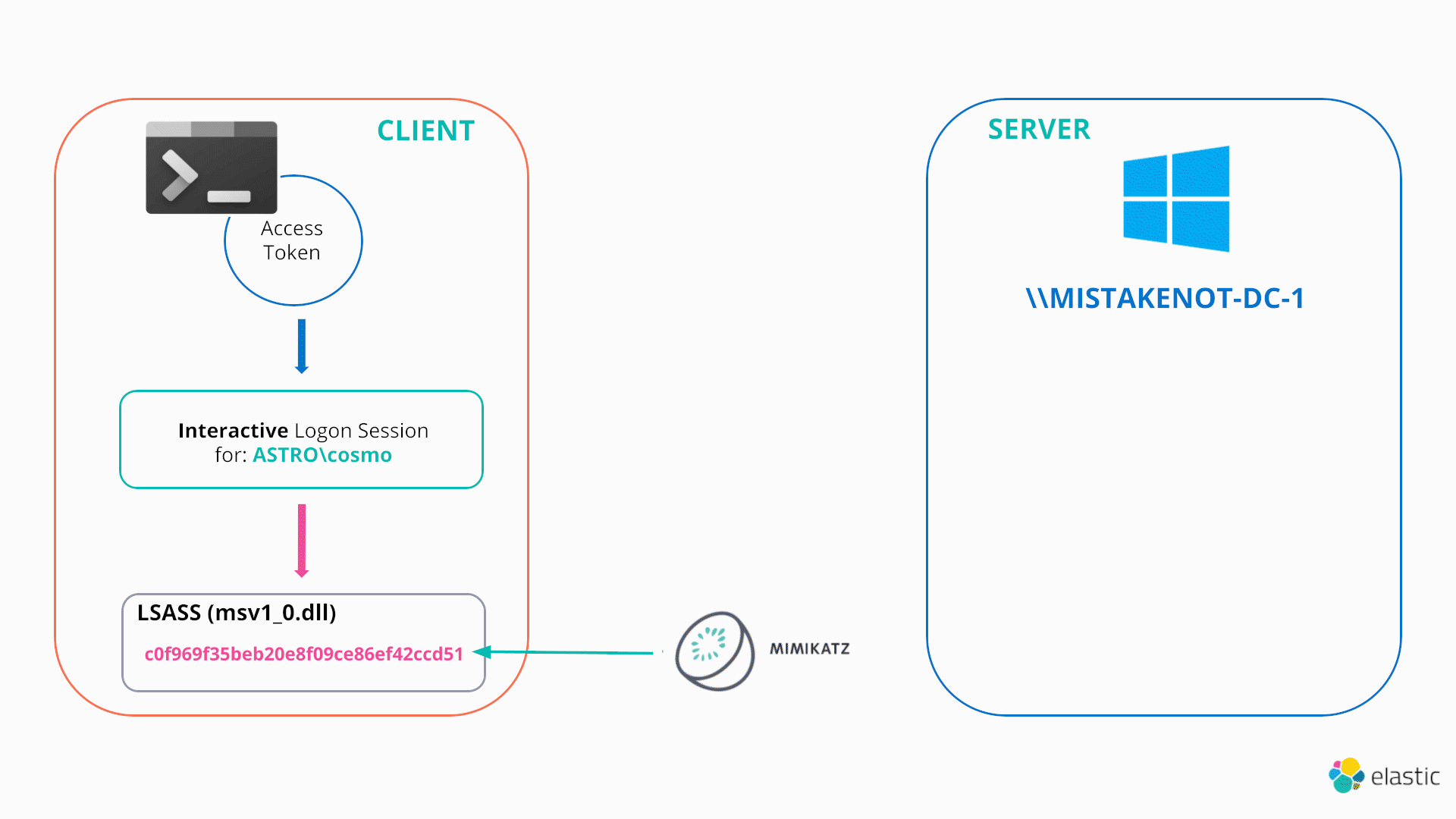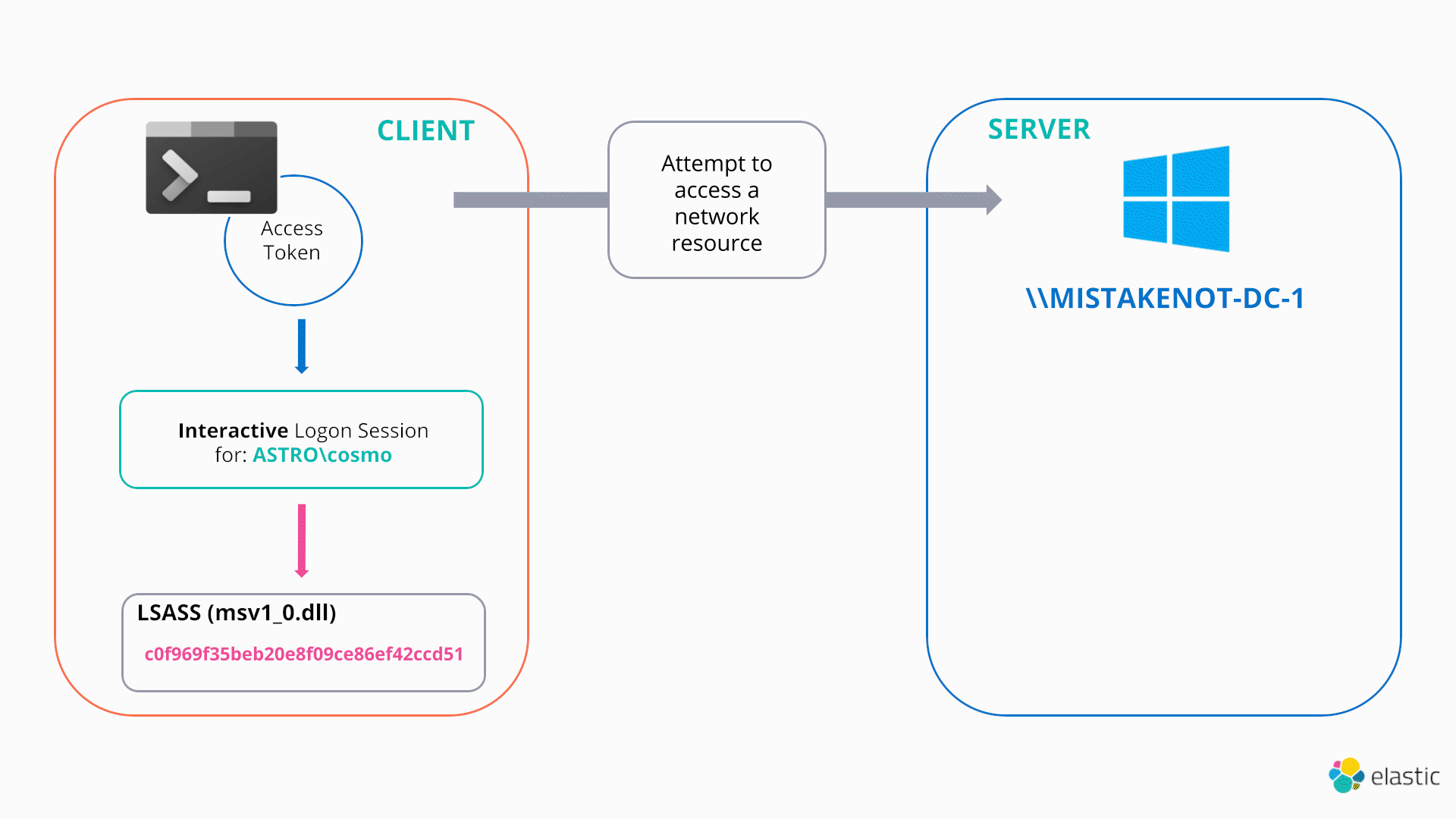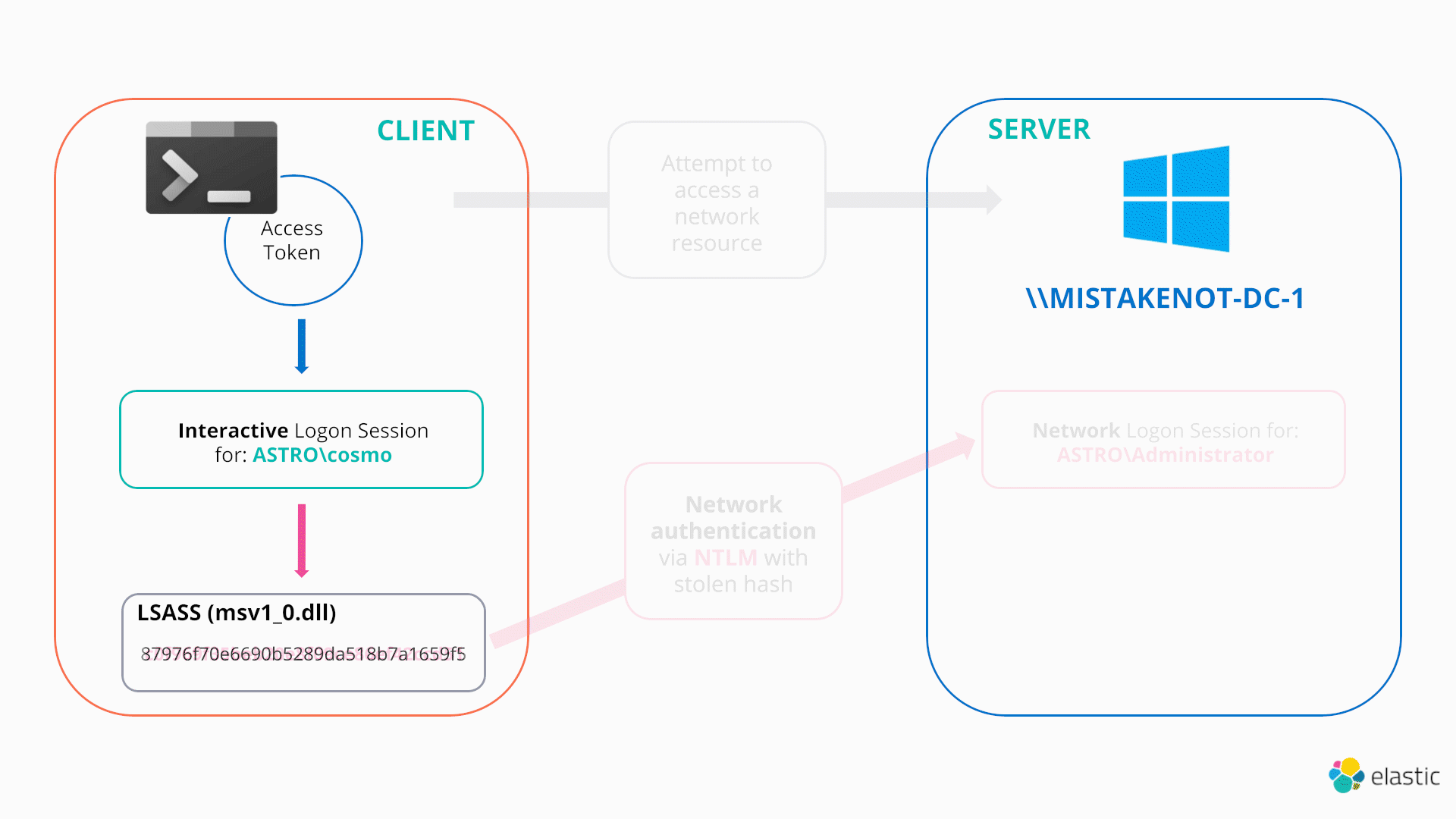
How attackers abuse Access Token Manipulation (ATT&CK T1134

Identity and Access Security
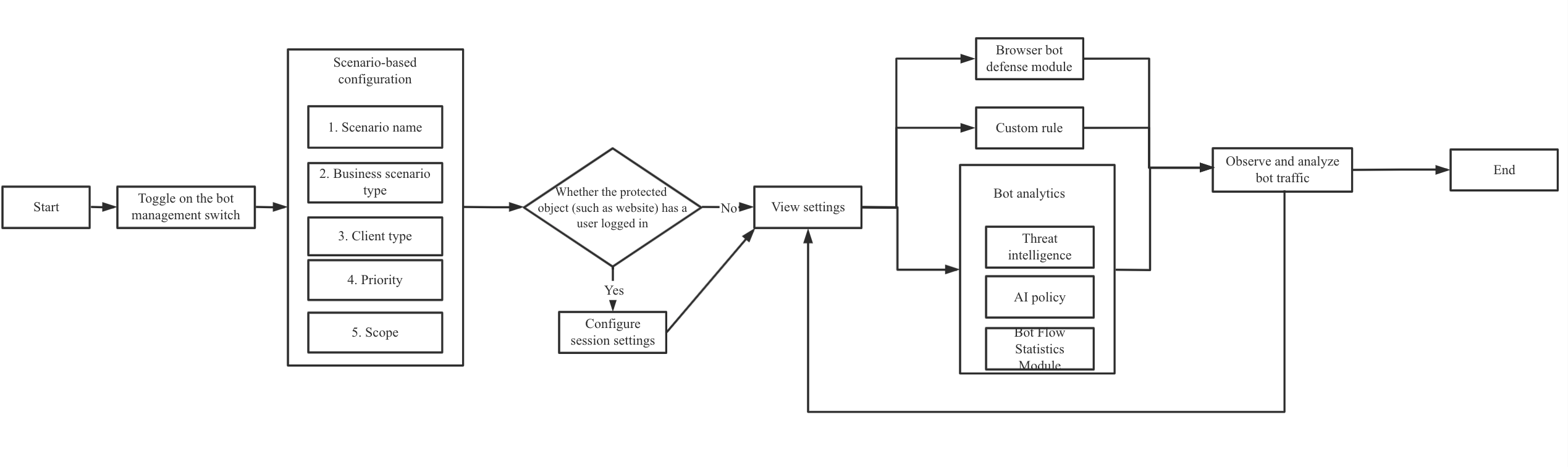
Best Practices of Scenario-Based Bot Configuration

Multi-factor authentication fatigue attacks are on the rise: How

Identity and Access Security
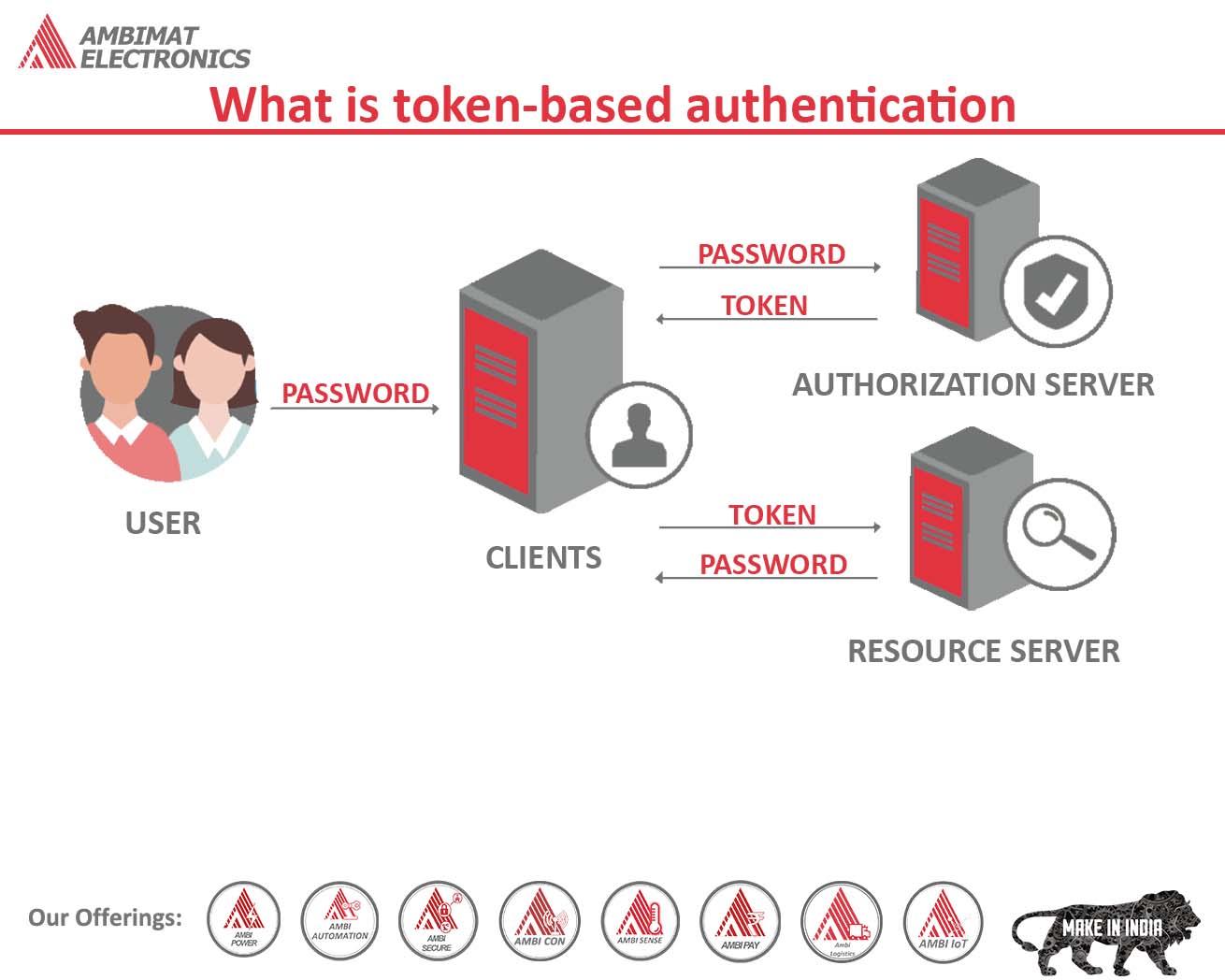
What is token-based authentication
You may also like








